UX DESIGN, Nov 2024
UX DESIGN, Nov 2024
UX DESIGN, Nov 2024
Frictionless Time Clock Page Management
Frictionless Time Clock Page Management
Frictionless Time Clock Page Management
Frictionless Time Clock Page Management
Simplifying the management of tokens for clocking-in sessions on an HR SaaS platform.
Simplifying the management of tokens for clocking-in sessions on an HR SaaS platform.
Simplifying the management of tokens for clocking-in sessions on an HR SaaS platform.
Simplifying the management of tokens for clocking-in sessions on an HR SaaS platform.
Client
Comunix is an integrated HR operations platform that was created to centralise the connection between companies and their employees.
As part of the project's expansion, the Time Clock initiative came along, which I was tasked with mapping out and developing as a solution, approaching it on interaction and user experience levels.
Comunix, as a company, previously belonged to the RB Serviços group, but soon grew to the point where it needed to be managed separately.

Comunix’s logo, 2024.
Challenge
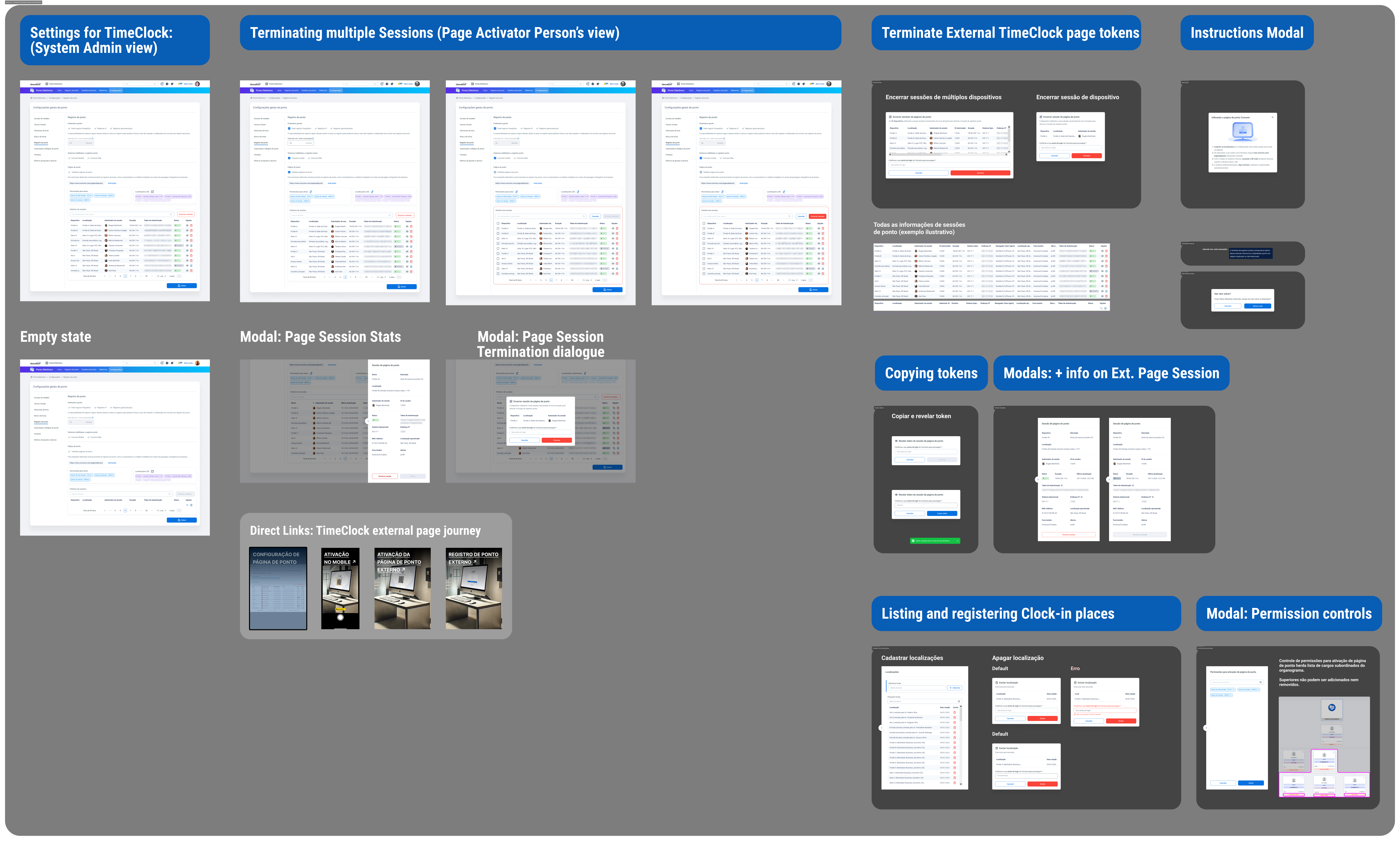
We were about to develop a solution for an external Time-Clock page, separate from the Electronic Time Clock Module. It works like a virtual Electronic Time Recorder, to be used, for example, on tablets in company corridors. Roles involved in this process:
- System Supervisor;
- Time Card Page Activators;
- Employees to clock in.
The recently departed Tech Lead had left a logic in which the System Supervisor person generated and monitored a series of tokens that served as logins, combined with randomly generated passwords to be distributed to Time Card Session Activators. This process was intended to untie the activator from the activation credential, so as to make resigning one less obstacle. However, the management of these tokens and passwords was not only complex, but also insecure and incomplete, because the distribution of passwords did not find a secure enough channel, since any way of transferring them, whether by email, message or in person, left security gaps in the very problem that the idea of authentication processes try to solve.
We needed to quickly change the course of the solution in time for it to be implemented.
My role
Product Designer
Platforms
Platforms
Cross platform: Web Desktop, Web Tablets, Mobile Phone App.
Year & duration
Year & duration
2024, 2 weeks + familiarisation time with other projects in the system (5 months designing other functionalities and getting to know the system and other modules)
Approach
Research and mapping
I analysed and redesigned the workflows of system supervisors, session activators and employees who clock in to identify problem areas and security vulnerabilities.
Tools: User Flowcharts and Service Blueprints.
I analysed and redesigned the workflows of system supervisors, session activators and employees who clock in to identify problem areas and security vulnerabilities.
Tools: User Flowcharts and Service Blueprints.

Re-use
The page was already designed and implemented, as it was directly supervised by the former Tech Lead together with the developers. I tried to make the most of what made sense from the point of view of interface standards and tables.
Communication
Secure authentication
Communication
Being a highly technological solution, and involving many concepts that were not very tangible to me, I needed to validate all the points of contact and availability of the necessary technology with System Architects and Product Managers. It may seem obvious, but it's worth pointing out that there was a lot of back and forth, as it required adjustments.
Tangibilisation
In order to reduce noise in communication, I prototyped all the stages of the solution, presented it, took feedback and adjusted it, making sure that the concepts of the solution were commonly understood.
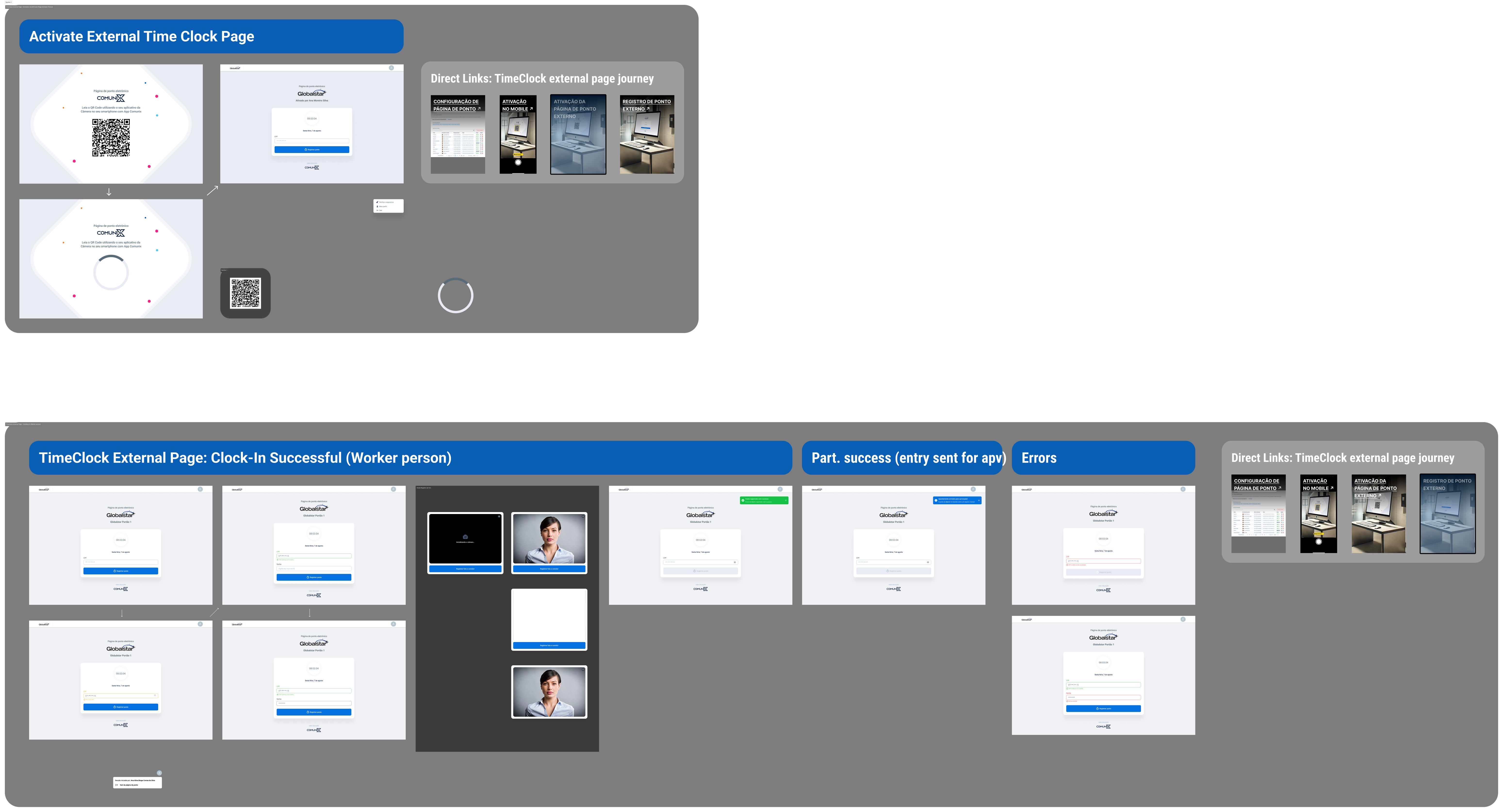
Solution
Simplification
Simplification
I introduced a permanent, easy-to-use link, to be defined by the administrator, on the same token management page (e.g. company.com/clock-in-page). Accessing the link would display a QR code, which would update every 5 minutes. The technology was already available in another module.
Secure authentication
Secure authentication
It allowed session activators to scan the QR code with their personal mobile apps, authenticate the session on them and thus activate the token on the dedicated clocking-in devices, without exposing any tokens and passwords on these shared machines.
Readjusted monitoring
Readjusted monitoring
I kept and reused the control table for system supervisors to view active sessions, including details such as activator identity, session times and activation dates, with options to deactivate compromised tokens/sessions.
Outcomes
The redesign simplified the process of activating the time pages, strengthened security by eliminating the use of shared tokens and passwords, significantly reduced the complexity of the solution and gave the system supervisors better oversight of active sessions.
The developers had already made the solution recently as previously assigned, but the CIO, Tech Manager reviewed and approved the solution I proposed. It was placed in the queue of future stories to go into development.
The redesign simplified the process of activating the clock-in pages, strengthened security by eliminating the use of shared tokens and passwords, significantly reduced the complexity of the solution and provided system supervisors with better oversight of active sessions.
CIO, Tech Manager and developers reviewed and approved the solution I proposed, but due to the prioritisation of more urgent demands, it was put on the backlog.
Thanks for visiting!
© Copyright 2024. Ígor Jales - UI/UX Designer